PGP is a #Asymmetric Cryptographic program used to encrypt, decrypt and sign emails over insecure transmission channel such as Internet with Digital Signature# which is developed by Philip R. Zimmermann in 1991. It has become the de facto #standard for email security. It provides five services: Confidentiality#, Authentication#, compression, e-mail compatibility (encode raw binary to ASCII characters using Radix-64 Encoding#) and segmentation (if the message is too large). It guarantees the security in Application Layer#.
Generally, it uses four types of keys: one-time session symmetric keys, public keys, private keys, and passphrase-based symmetric keys. The public key could be identified using the least significant 64-bits of the key which is most likely to be unique. It will be transmitted to the network with the key ID instead of the whole key for efficiency’s sake. The security of the private key is depended on the passphrase.
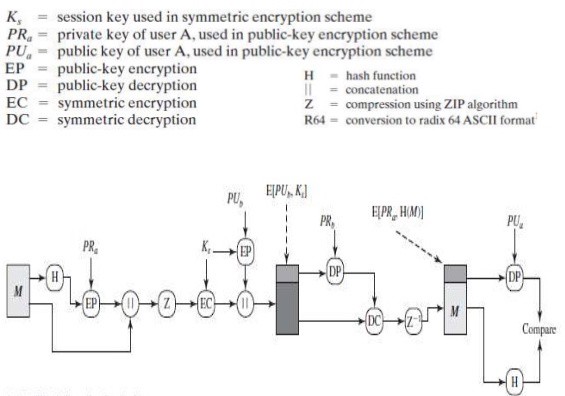
Process
Authentication, that is validation of the sender, is done by involving the sender’s private key \(KR_a\) and public key \(KU_a\), and comparing the hashed message \(H(M)\)and the decrypted plaintext \(M\). The confidentiality of the message is done through the compression \(Z\) and encryption of the message using a randomly generated session key \(K_S\) (with ANSI X12.17 generator) which will be distributed together with the message encrypted by the receiver public key \(KU_b\).
The following steps show the entire process:
- The sender creates a message
- A Hash Function such as SHA-1 will be used to generate a hash code version of the message
- The hash code is encrypted with Rivest-Shamir-Adleman (RSA)# using the sender’s private key.
- The hash code then concatenates with the plaintext message with it being the top of the plaintext.
- The message is then be compressed, thus finish the authentication process and start the confidentiality on the sender side.
- A random 128-bit number will be generated to be used as a one time session key.
- The message then is encrypted using CAST-128, #International Data Encryption Algorithm (IDEA) or #Triple Data Encryption Standard (3DES) with the session key.
- The session key is encrypted with Rivest-Shamir-Adleman (RSA)# using the recipient public key.
- The encrypted session key will then be prepended to the encrypted message, thus complete the confidentiality process on the sender side.
- When the recipient received the encrypted PGP message, it will first decrypt the session key using their private key (\(KR_b\)) and Rivest-Shamir-Adleman (RSA)#.
- The recovered session key will then be used to decrypt the message.
- The message will be decompressed, thus complete the confidentiality process on the recipient side.
- The recipient uses Rivest-Shamir-Adleman (RSA)# with sender’s public key to decrypt and recover the hash code.
- A new hash code is generated from the plaintext message and used to compare with the decrypted hash code. If two match, then message is authenticated.